Bojie Li (李博杰)
2014-11-20
C 程序为什么要编译才能执行?一个 C 程序在变成可执行文件的过程中,为什么要经过预处理、编译、汇编、链接这四道工序?让我们从这段简单的 C 程序开始。
为什么要编译
这并不是一个简单的问题。我们知道 Python 代码不需要 “编译”,输入一行代码就可以运行出结果了,对用户很友好有木有!这种交互式的运行环境被称为 REPL(Read-Evaluate-Print-Loop),也就是读取用户输入的语句,执行语句,输出语句的值,再返回到等待输入状态。
2014-11-19
2014 年 9 月 19 日 22:30。我拖着半人重的行李箱,在科大西区斑驳的树影里独行。就在几个小时前,我还在研究背包问题:在背包容积限制下,如何把尽可能有价值的东西带回来。
当时,只有很少几个人知道我回来了:组里的老板和同事、我爸妈,还有张静宁。就在几天前,LUG 小伙伴们还在讨论我十月份会不会回来:由于搞挂 mirrors 服务器,我还欠大伙一顿饭呢!
这是 10 月 20 日写的生活总结《逃离活动室》本来的开头。但觉得不合适,就换成了 “逃离微软”。本月初我把人人封面照片换成了 9 月 20 日 SFD 的工作人员合影,就是为了纪念这一年新生活的开始。

2014-11-09
说起 Ken Thompson,我们首先想到的是他发明的 UNIX 操作系统。他因此获得 1984 年的图灵奖。在图灵奖演讲上,Ken Thompson 提出了一个深刻的问题:看到了软件的源码,就意味着没有后门吗?编译器是否可能存在能自我复制的后门?
这篇发表在《ACM 通讯》上的论文只有短短三页,省略了很多细节。原理上有点像输出自身代码的 C 程序,但又比它难很多。我追随先哲的脚步,给一个开源 C 编译器——tcc 插入了能自我复制的后门,这个插入了后门的编译器在编译 Linux 登录程序 sulogin 的源码时,会自动插入一个后门。
2014-11-05
前天张擎宇同学告诉我,在有 Wi-Fi 的时候最好使用 Wi-Fi 并关掉 3G 网络,可以省很多电。3G 真的比 Wi-Fi 费电吗?我查阅了文献,发现果真如此。当要传输的数据较少时,电源消耗的差距可以大到 10 倍之多。
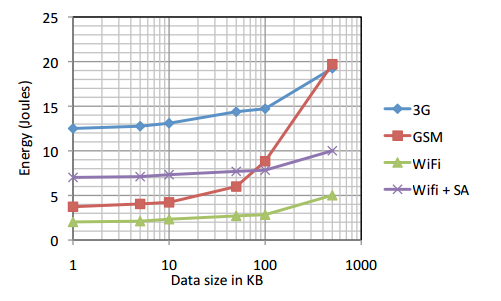 蓝线:3G 功耗;绿线:wifi 功耗;紫线:考虑了 wifi 扫描和建立连接之后的功耗(来源:TailEnder)
蓝线:3G 功耗;绿线:wifi 功耗;紫线:考虑了 wifi 扫描和建立连接之后的功耗(来源:TailEnder)
原因主要有两方面:
- 3G 网络完成数据传输后要保持一段时间的高功率状态;
- 3G 网络的发射功率远大于 Wi-Fi 网络。
2014-10-29
凡是 LUG 的活跃会员,都早晚会被吸引进码农的圈子。
这个谣言的出处及真假暂不考证。到底是 LUG 的氛围把小伙伴们引上了码农这条不归路,还是打定了主意走码农路的才会长期活跃在 LUG,我说不清。
为什么选择计算机专业,事实上是两个命题:
- 为什么选择计算机作为未来的职业?
- 为什么本科期间选择计算机专业?
我试图用自己的经历来解读这两个命题。少年时代,我曾把科学家作为自己的梦想,高三那会儿想的是做理论计算机研究。在大一升大二的关头,我曾在数学和计算机之间徘徊抉择,还曾考虑过学物理。因为想不清楚,大一下学期的时候我并没有申请转专业。在大二上学期开学一周后,我感觉不能继续混沌下去了,于是提交了转专业申请,从第二周开始,踏上了码农的不归路。
2014-10-20
逃离微软
2014 年 9 月 17 日上午,微软亚洲研究院 12 楼会议室。老板刚结束了一个月的国际会议回到北京,我在组会上忐忑地汇报一个月来并不令人满意的进展。这之前的几天我的心一直在狂跳,生怕老板看穿我不认真干活的本质。出人意料的是,老板在汇报结束后并没有骂我,而是说我的模型比起一个月前有了很大进步。不过,我们都清楚地认识到我们的工作不可能赶上 9 月 26 日截止的 NSDI 会议了。
2014-09-29
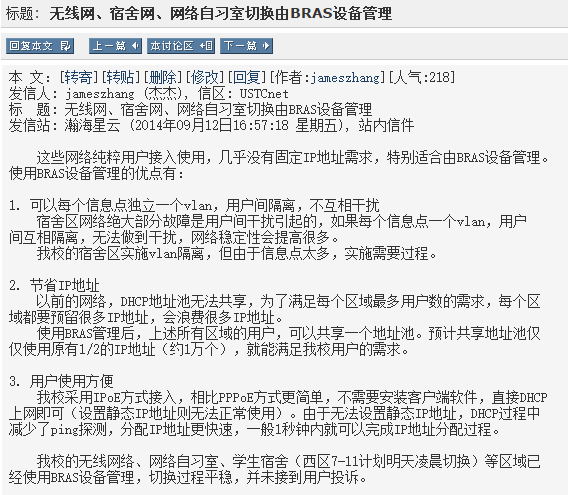
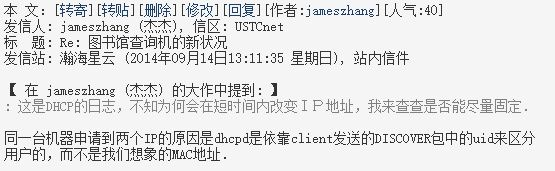
DHCP 的麻烦事
事情要从科大更新网络接入管理设备说起。
公共上网区域之所以要统一分配 IP 地址,是因为早先各楼各自为政、零散分配的 IP 地址段不够用了。几年前上网的主力是台式机和笔记本,也不可能时时刻刻开机;但现在人人都有智能终端,有可能还不止一台,到哪里就会连上哪里的 Wi-Fi。很多地方早先绰绰有余的 /24 地址段(256 个 IP)在高峰时段出现了分配不到 IP 的情况。而科大的 IP 地址池大小是有限的,集中分配就解决了地址不够的问题。
这本来是件皆大欢喜的事情,但新设备带来了新的问题。采用网络启动的图书馆查询机隔一段时间就卡死了,原因是母系统启动阶段与子系统启动阶段所分配到的 IP 地址不同,而这种不同又是由于 BRAS 网络接入管理设备的 bug。
2014-07-06
使用 ext 文件系统存储数据的同学也许发现,200 G 的分区只能用 190 G,2000 GB 的分区只能用 1900 GB。这 5% 磁盘空间到哪里去了?有的同学认为这是 1000 进制与 1024 进制的区别,但事实并非如此。
1 | $ df /mnt/sdb/ |
上面这块标称 2 T 的磁盘可用空间为 0,看起来是满了。试着创建一个目录,发现没有空间了。
1 | $ mkdir hello |
但 sudo mkdir hello 竟然能成功!这是怎么回事呢?答案在 ext 文件系统的 “预留空间” 里。
2014-06-22
看着离校手续单上 “结清网络费” 一栏的 “免办”,我思绪万千。我也许是少有的几个从未开通过 “网络通” 的学生之一。因为在少院机房不需要网络通,后来有了 LUG 服务器也不再需要网络通,现在我坐在寝室里,用无线信号放大器蹭东活的 ustcnet。其实我并不真的在乎每月 20 元的网络费,不开网络通,更多是一种符号、一种象征,它串联起支离破碎的记忆,祭奠着悄然逝去的青春。纯属个人 YY,勿喷。
10 年前:编程从谭浩强开始
刚上初中的时候,听说有计算机竞赛这个玩意。不知道是哪里来的消息,我家长以为计算机竞赛就是玩游戏,当时我也不知道百度一下,就信以为真了。开课一个月之后,孟同学跟我说,计算机竞赛里有很多像奥数题,你应该喜欢。我家长于是向班主任核实,才知道计算机竞赛是编程序,其实我当时对编程序的理解就是修电脑的叔叔在黑框框里输入命令。当我上大学之后教同学做网站的时候,她也把 Windows 命令提示符说成是黑框框,我不禁哑然失笑,其实我们都是从那里走来的。
第一次去上计算机竞赛课的时候,40 个机位的机房里挤了 60 多号人,我连座位都没有;老师在黑板上讲 printf,台下的同学昏昏欲睡。看到同学们人手一本绿皮的《C 程序设计》第二版,封面上印着“发行 700 万册”,我就感觉谭浩强是仅次于比尔盖茨的计算机大神了。听说大牛学长还买了《算法导论》,虽然有点贵,还是“请”了一本回来供着;之所以供着是因为上面没有可以直接抄的 C 代码,没有代码的书能叫计算机专业书吗?
2014-06-01
Traditional router requires cold reboot if any component of the router software fails or needs to be upgraded. Network traffic is likely to be interrupted for minutes in the meantime. This work designs and implements a fault-tolerant software architecture composed of four components: clients including routing protocols and administrator, the router information base (MiniDB), a daemon to resolve rule conflicts among clients (SyncD) and the SDK for programmable switching chip. This architecture allows any component to fail or upgrade without interrupting data plane, and the control plane will automatically recover within predictable time after the component restarts.
Publication
Dissertation of Bachelor’s Degree, 2014. [PDF (Chinese)]
People
- Bojie Li, 4th year undergraduate in USTC
- Dr. Kun Tan, Senior Researcher in Microsoft Research Asia