Bojie Li
2023-01-22

Time: May 1, 2023, 10:58
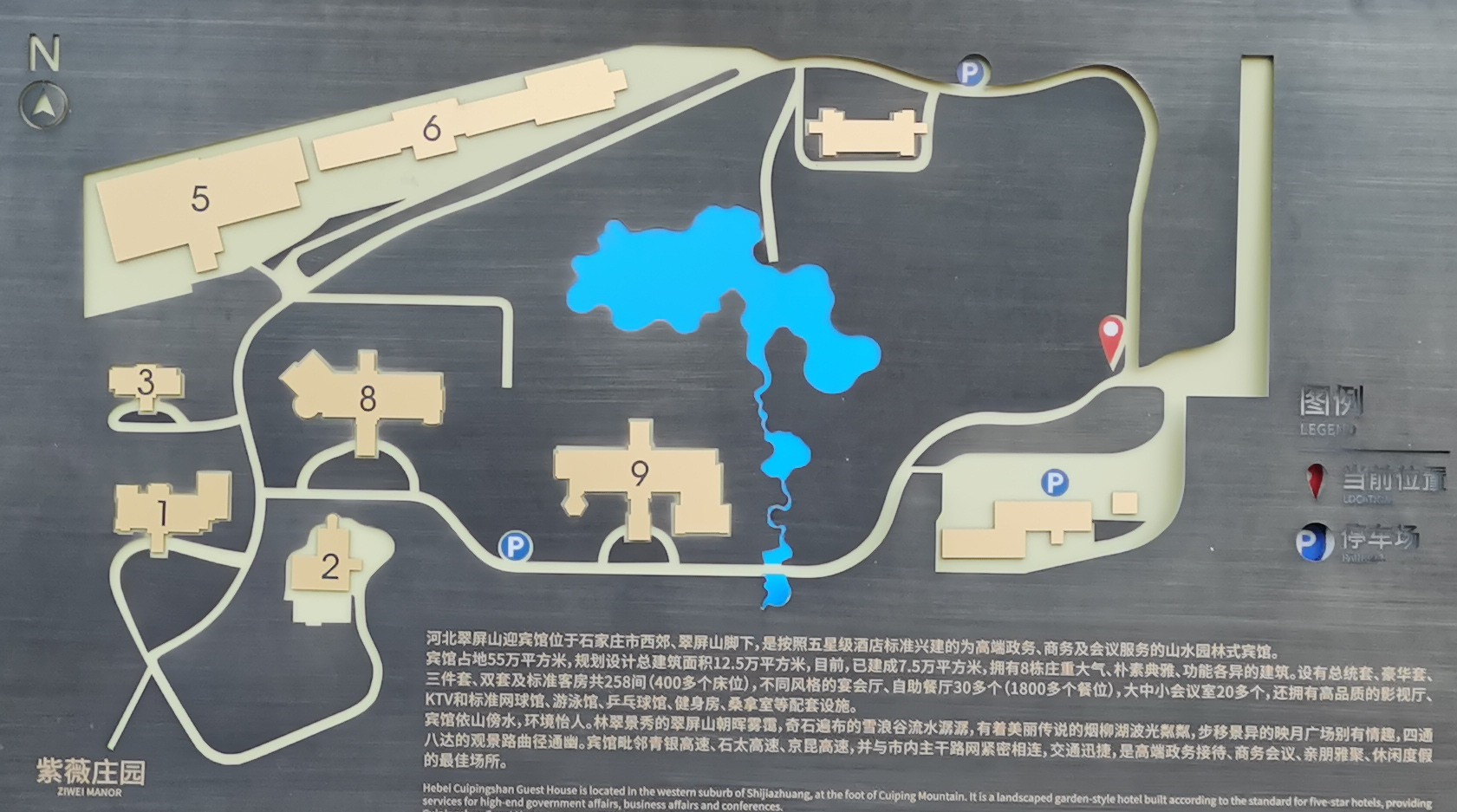
Location: Cui Ping Shan Hotel, Hebei
Transportation Information: Cui Ping Shan Hotel is located at No. 1 Yingbin Road, Luquan District, Shijiazhuang City, Hebei Province.
- As Cui Ping Shan Hotel is located in the western suburbs and is not accessible by subway, public transportation is inconvenient. It is recommended to take a taxi.
- High-speed rail:
- By car: The nearest route from Shijiazhuang High-speed Rail Station is 16 kilometers, and the elevated route is 22 kilometers. It takes about 35 minutes by car without traffic.
- Public transportation: You can take bus 320 / air 320 directly (need to walk 1.3 kilometers), which takes 1 hour and 20 minutes; or take subway line 3 to subway line 1 to tourist bus 5, which takes 1 hour and 10 minutes.
- The taxi queue at Shijiazhuang High-speed Rail Station is very long after 22:00. If you arrive late, it is recommended to contact us in advance for pick-up.
- Airplane:
- By car: It is 53 kilometers from Shijiazhuang Zhengding International Airport, and it takes about 50 minutes by car without traffic.
- Public transportation: From Zhengding Airport, you can take Airport Bus Line 1 (one bus per hour) to Subway Line 1 to Tourist Bus 5, which takes 2 hours and 10 minutes.
- It is inconvenient to take a taxi at Zhengding Airport at night. If you arrive late, it is recommended to contact us in advance for pick-up.
- As the wedding officially begins at 10:58, it is recommended to arrive in Shijiazhuang on April 30. Those departing from Beijing who are short on time can also consider taking the early high-speed rail on May 1 (5 departures from 06:26 to 08:34).

Accommodation Information:
- Try to arrange to stay in Building 6 and Building 9 of Cui Ping Shan Hotel, Hebei, where rooms have been reserved. If there are special circumstances, we will arrange nearby hotels.
- Breakfast is expected to be in Building 6, from 7:00 to 10:00. Bridesmaids, groomsmen, and staff need to leave early and will not have time for breakfast, so a simple meal will be arranged in Buildings 6 and 9.
- The distance between Building 6 and Building 9 is 560 meters, and it takes 8 minutes to walk.
2022-12-13
There’s a classic joke where a student chose a course called “Choices and Future”, only to find out in the classroom that it was about “Options and Futures”, because their English names are both Options and Futures. A few days ago, the hotel where I had a meeting was right across from the Shanghai Futures Exchange, which made me think of a question: What are our judgments and choices about the future based on?
Recently, I read two books, “Gifts Differing” and “How NASA Builds Teams”, and found that this reflects the differences in people’s ways of thinking. Sensing and iNtuition, Thinking and Feeling are the two most critical differences.
Before the main text, you might want to think about the differences in the characters of Sun Wukong, Zhu Bajie, Tang Monk, and Sha Monk in “Journey to the West”, and how they work together as a team?
2022-12-12
Thanks to Professor Xu Chenren and Professor Huang Qun for the invitation, I am very honored to have given a guest lecture for the Computer Network course at Peking University on December 12, 2022.
Abstract: Data center networks, wide area networks, and wireless networks provide the communication cornerstone for the intelligent world of Internet of Things.
Data center networks have traditionally been designed for easily parallelizable web services. But today, AI, big data, HPC are all large-scale heterogeneous parallel computing systems, which have high requirements for communication performance. The heavy software stack causes huge overhead, which requires the communication semantics of data center networks to evolve from byte streams to memory semantics including message semantics, synchronous and asynchronous remote memory access, RPC, and to achieve extreme latency and bandwidth with a combination of software and hardware. In the future, we hope to treat the data center as a computer, on the one hand, to achieve peer-to-peer direct access between heterogeneous computing and storage devices, making the data center interconnection as high-performance as the internal bus of the host; on the other hand, to make distributed system programming as convenient as single-machine programming through Serverless.
Large-scale live streaming and short video on-demand, real-time audio and video communication and other applications pose new challenges to the stability of wide area network transmission. Internet giants have built their own global acceleration networks and designed new transport protocols such as QUIC to achieve a high-quality user experience. In addition, due to the low energy cost in the western part of our country, the strategy of “computing in the east and calculating in the west” has become a national strategy. Through Regionless scheduling, we can achieve a “nationwide integrated large data center”.
Seamless collaboration of intelligent terminals such as mobile phones, PCs, wearable devices, smart homes, smart cars, and industrial Internet applications such as 5G to B all require stable low latency and high bandwidth, which requires wireless protocol stack optimization, and even wireless memory semantics to support Gbps-level bandwidth. In addition, through the “distributed super terminal” programming framework of HarmonyOS, more closely distributed collaboration can be enabled to achieve seamless data and service flow.
Download Slides PDF (Updated on 2022-12-15)
Download Slides PPTX (Updated on 2022-12-15)
Full text of the speech:
2022-12-10
Recently, everyone has been playing with ChatGPT, which is really impressive. Although it’s not omnipotent, it’s the first AI dialogue system that doesn’t feel like an artificial idiot to me. It handles difficult problems such as reference and memory context very well. Especially in programming problems, it is sometimes more useful than StackOverflow. If my candidates performed like this, I would definitely prioritize hiring them.
The main shortcomings of ChatGPT currently are:
- The knowledge base is not updated enough and the coverage is not comprehensive. It cannot answer recent events or more obscure knowledge. It is suggested to combine it with a search engine or knowledge graph, first use the prompt word to search for some results, and then use NLP methods to integrate the search results. It is said that some research teams are already working in this direction.
- Lack of logical reasoning ability, slightly complex logic can easily get wrong, and answer seriously when it’s wrong. How to solve arbitrarily complex logical problems is a big challenge. It’s even harder to recognize answers that seem correct but are actually absurd.
- Currently, it only supports text and does not support multimodal. Now you can let ChatGPT generate prompts, and then input them into DALL-E to generate images. In the future, generative models that support multimodal input and multimodal output will make human-computer interaction more natural and may become the next generation of human-computer interaction paradigm.
- The cost of a single answer is currently high, requiring several cents, significantly higher than the cost of a Google search. If the cost can be reduced through algorithm or hardware improvements, or if new business models can be created by combining with recommendations and advertisements, there will be room for commercial profit.
This year can be said to be the “first year” of AI-generated content. A few months ago, we were all shocked by the stable diffusion (DALL-E 2) in the CV field, and now ChatGPT has set a new SOTA for NLP. Stable diffusion and ChatGPT are both done by OpenAI, and the financial backer behind OpenAI is Microsoft, which can be considered as an important game that Microsoft has won back in the AI field. In previous years, it was always Google Deepmind’s Alpha series that stole the limelight, from Go to proteins and matrix calculations.
The intelligent assistant that can communicate naturally with people is a scene in countless science fiction movies, and it is also a vision set by major companies 20 years ago. Today, we finally see the dawn of becoming a reality. Intelligent assistants may give birth to the next trillion-dollar industry, just like mobile internet has overturned PC internet and video has overturned text, becoming a new paradigm of human-computer interaction and profoundly changing human work and life.
Below are some examples I tried in ChatGPT:
2022-12-10
Firstly, it is the scale of business. Due to geographical and cultural reasons, most domestic companies encounter some difficulties in going global, mainly in the domestic market, which is much smaller than the European and American markets. The same is true for public clouds, where the revenue and market value of AWS, Azure, and Google Cloud in the European and American markets are higher than those of Alibaba, Tencent, and Huawei Cloud in China. Since the development cost can basically be shared, the average salary of developers in American companies is higher than that in China, which can hire relatively more excellent talents; it can also generate more profits to support relatively long-term research, such as OpenAI, Deepmind, and Microsoft Research. Breakthrough innovations like ChatGPT are hard to come from product departments with intense development rhythms, they usually come from research departments without much short-term commercial monetization pressure.
2022-09-03
Text content to be supplemented, let’s put out a few photos first~
2022-07-27
Computer Network & Protocol Laboratory
Huawei’s Computer Network & Protocol Laboratory is a subsidiary of the Distributed and Parallel Software Laboratory of the Central Software Institute of the 2012 Laboratory, with locations in Beijing, Shanghai, Hangzhou, Shenzhen, and Tel Aviv, Israel.
Vision: Rooted in laying the foundation stone, innovation leads the future of distributed communication
Positioning: Huawei’s software engine in the field of computer network and protocol technology, covering theoretical breakthroughs, technological inventions, technological innovations, and quality delivery. Standing at the forefront of this technical field, we research and break through world-class technical problems in computing native networks and wide-area network deterministic communication, build an industry-leading full stack of distributed communication, and work with ICT, terminal, cloud, intelligent car and other main product teams to build differentiated communication competitiveness, gradually grow the industrial ecosystem, and help business success.
Team: A high-level innovation team composed of top industry-leading experts, genius youngsters, PhDs, and engineers mixed special forces, overseas legions. The technical research results are significant. Since 2018, 5 papers have been accepted by SIGCOMM, the top global network communication conference; and key technologies have been selected into Huawei’s top 10 inventions for three consecutive sessions.
2022-07-22
How many trips per year?
Since 2012, up to now, I have been to … cities, and traveled … times (going from city A to city B counts as one trip; if I go back to city A again, that counts as two).
Which cities have I stayed in the longest?
Note: If I enter on January 1 and leave on January 2, it is counted as 2 days, so there is double counting and the total number of days exceeds the number of calendar days.
If we consider all cities except Beijing and Hefei as travel (including business trips), then the total number of travel days accounts for …, in total … days.
2022-07-03
This article summarizes the technical architecture of USTC iCourse.club. Founded in 2015, iCourse is a Flask-based website aiming at rating courses in USTC (University of Science and Technology of China). Although it is only a small website from a technical point of view, it offers a glimpse of the architecture of a typical web service.
2022-06-27
USTC LUG GitLab will soon stop serving non-campus users. Although I have a campus email, to prevent sudden disconnection one day, I have backed up all my repositories locally and hung the public repositories on GitHub. As the first user of LUG GitLab, I have a total of 209 repositories, 123 of which are personal repositories. LUG GitLab was established on March 14, 2013 (Pi Day) and has been running for 9 years, even slightly earlier than Telegram. GitLab and VPN are the longest-running (9 years) network services I have established, serving thousands of users. I have long left the management and operation team, but I still have a lot of feelings for these services.
My GitHub homepage: https://github.com/bojieli
My USTC LUG GitLab homepage: https://git.lug.ustc.edu.cn/boj
These public repositories are mainly the course assignments I did at USTC, various undergraduate projects, and network services I did at LUG. Most of the projects I did during my PhD at MSRA have not been open-sourced. I only released the source code of SocksDirect and the LaTeX source code of several papers, some of which have been anonymized and do not retain internal commit information. The source code after work is even less likely to be made public at will. The already open-sourced MindSpore AKG project also anonymized the internal commit information when it was open-sourced (internal contributors after open-sourcing are directly developing on the public repo, but I have left the AKG project after open-sourcing).
Therefore, from the contributions on GitHub, you can see that the most contributions were in 2016, with 2000+ contributions; last year and the year before, there were only a pitiful number of contributions; there were 1000+ contributions from 2013-2015; only a few hundred from 2017-2019, one reason is that the project was not open-sourced, and the other is that I personally was somewhat detached from the front line of coding, pondering new research ideas all day, becoming a PPT engineer, and not spending much time on actually coding to implement ideas, which is also why I published fewer papers in the later stages of my PhD.