Security
2015-08-02
On July 28, 2015, bind9, the most widely used DNS server in the world, exposed a serious denial of service vulnerability (CVE-2015-5477).
A bit of background knowledge: DNS is a service that maps domain names to IP addresses. When you visit google.com, your computer will ask the DNS server in your area, what is the IP address of google.com? If your neighbor happens to be visiting google.com, the DNS server will directly return its IP; otherwise, this DNS server will ask Google’s official DNS server, get the IP address of google.com, and return it to you. The DNS server in this area is called recursive DNS; if the recursive DNS is down, it will cause the area it serves to be unable to access the internet. Google’s official DNS server is called authoritative DNS; if the authoritative DNS is down, it will cause the websites it serves to disappear from the earth.
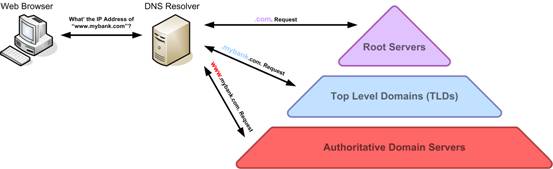
DNS Recursive Query (Image Source)
How serious is this vulnerability? Just send a UDP data packet, and you can take down a DNS server. Whether it’s recursive DNS or authoritative DNS, no matter what configuration bind9 has made, as long as this data packet is received by the bind9 process, it will immediately throw an exception and terminate the service.
2014-05-12
There are two types of passwords in the world: one is to prevent your little sister from peeking at your files; the other is to prevent the authorities from reading your files.
—— Bruce Schneier “Applied Cryptography”
The legendary “plaintext password” comes in two forms: plaintext transmission and plaintext storage. A password transmitted in plaintext does not necessarily mean it is stored in plaintext, and a password stored in plaintext does not necessarily mean it is transmitted in plaintext. The plaintext password incident that caused a stir last year was a case of passwords being stored in plaintext. Once the website’s database was stolen, the users’ passwords were also stolen. Transmitting passwords in plaintext is also very dangerous, as many places on the network may have sniffing devices installed. To these sniffers, passwords transmitted in plaintext are no secret at all. This article focuses on the security issues in password transmission.
What is “plaintext”? If a password is sent out directly in ASCII characters, it is plaintext to anyone; if a password is encoded with base64 (for example, 123456 encoded with base64 is MTIzNDU2), it may be ciphertext to most people, but it is plaintext to any professional programmer. Some people think that if the “encryption” algorithm is made more complex and the code is obfuscated, no one will be able to analyze it. This approach is called hiding, not security, and is at the level of preventing little sisters from peeking at files. Real security depends on public, widely used cryptographic algorithms, and relies on keys rather than the algorithm itself to ensure security.
Unfortunately, cryptographic algorithms and protocols are not necessarily secure just because they are cobbled together.